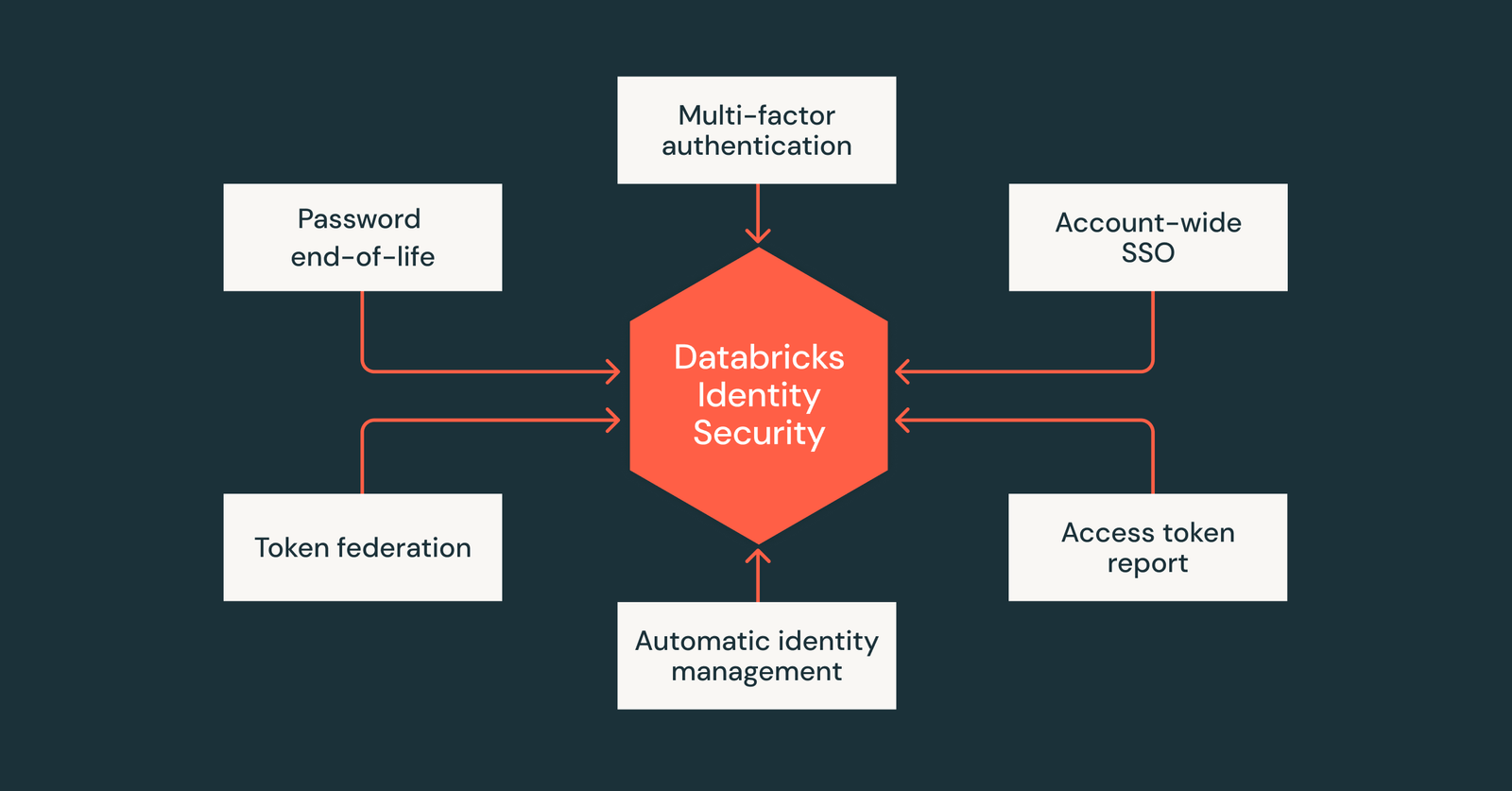
The future of identity security is without a password, a conscious context and friction-and continues to build this future on databricks. We have introduced new skills across Databricks Data Intelligence Platform To help customers strengthen verification, automate identity provision, and allow a safe program approach, which makes modern, scalable identity and access control facilitates.
Remind, Passwords Managed by Databricks He reached the end of his life on July 10, 2024 and have not been supported for a long time in the user interface or through the authentication of the API. To further support the future without a password, we also announce that it is available Multifactor Verification of Databricks-Management (MFA).
Given that more customers rely on Databricks to democratize data and AI access, ensuring the program approach is more important than. To reduce the long -term risk of API token, we have introduced several new checks:
- Automatic cancellation of personal access tokens (PATS) that are inactive for 90 days
- Maximum life 2 years for newly created PATS, so the credentials no longer stand for indefinitely by default
- General availability of access tokens that provides administrators deeper visibility of the use and risks of token
These updates are in line with the direction of developing industry standards, including NIST, PCI DSS and ISO, which move from the complexity of the password to smarter and more adaptive identity frames.
Here is a deeper immersion of what is new and how to make the most of it.
Simplify SSO management by unified login to AWS
We are moving all customers united loginWhere the SSO does not have to be configured at individual workspaces. Unified login immediately brings one login (SSO) to all databricks workspaces in all birthdays.
Unified login allows you to manage one SSO configuration at your account level. This means less overhead costs for administrators, it is access to the police for the user and the stronger overall safety holding. Combined with Emergency access SSO using MFAThe unified login also provides secure backup for administrators and provides centralized inspection without sacrificing flexibility.
The united login is already used in thousands of production space and customers should plan their migration. Since December 2024, all new SSO settings are automatically intended for the unified login by default. This makes it more efficient and easier to use new users to start using features such as AI/BI sharing, Genie and applications without further configuration. We recommend moving all work spaces to the unified ASAP login.

Proven procedures for authorizing united login
To use SSO one-time settings at your birthday level, make sure the identity provider (IDP) configurations allow all users of the workspace to the Databricks account. After completion, you can confidently choose any old working space to reuse SSOs at an account level with a unified login. FINLLY, Remove the outdated IDP tiles specific to the workspace to avoid confusion.
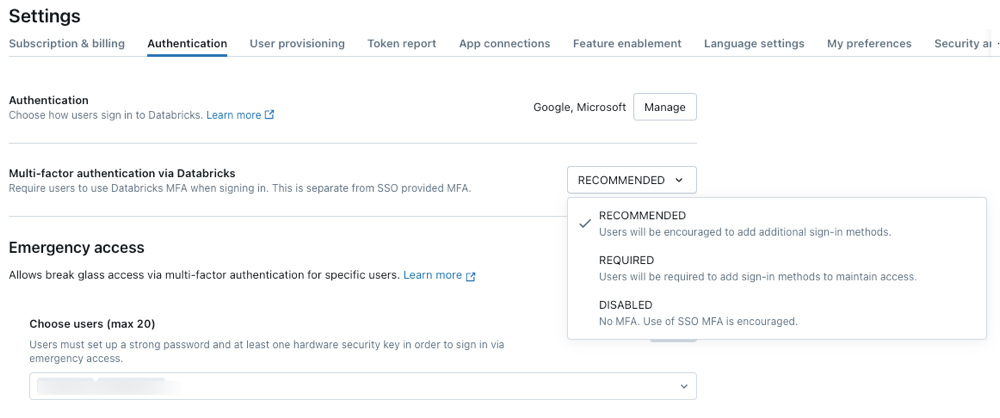
By default, be sure to use multi -factor verification of managed databricks (MFA)
SSO remains the best practice for centralized identity management. The MFA permit to the Identity Provider (IDP) is in line with your company’s security principles and provides access to your entire user base.
Were enthusiastic to introduce Databricks-de mfaNow generally available for all AWS accounts that have so far configured a single login (SSO). This new feature enables EN Enlurce administrators to authenticate (MFA) for all users and increases security throughout your organization. With support for popular Applicator Application and PassseysMFA settings are fast and easy. Administrators can allow this through the account console.
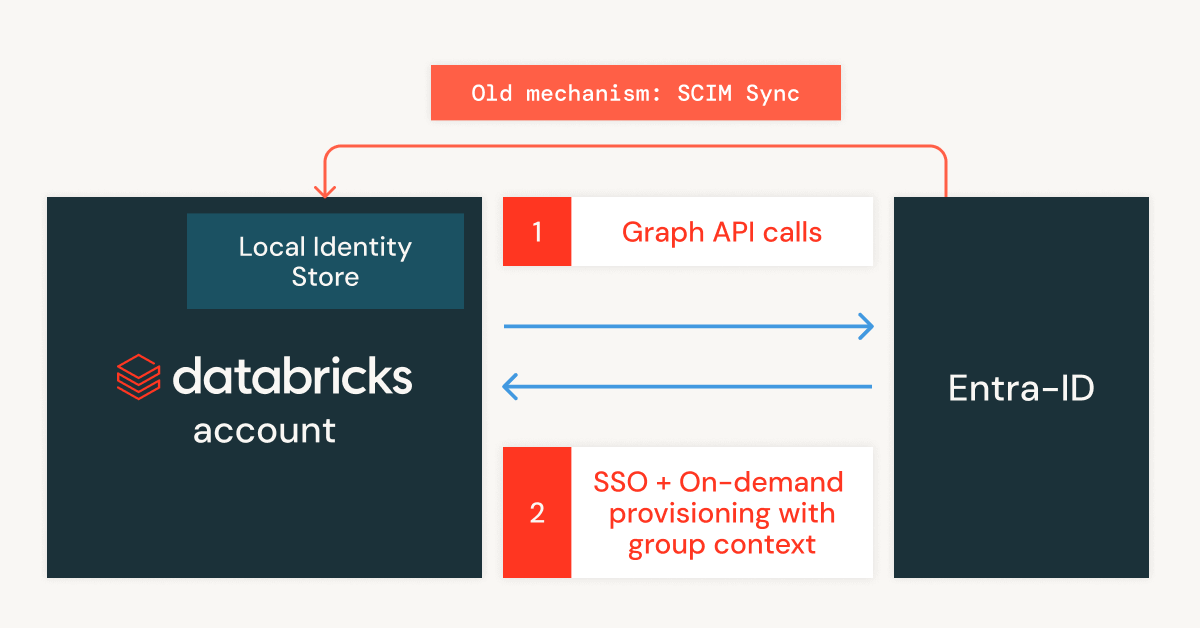
Fast provide new users on Azure Databricks with automatic identity management
Automatic Identity ManagementNow in a public preview for Microsoft input ID, it allows for secure management in real time natively intensively with users, groups and main service in ID Entra, no applications for connectors or manual synchronization are required. The best of all is also respectful of nested groups and groups containing network networks, including control of access across complex hierarchies.
One of our key applications is to simplify sharing Dashboards AI/BI gold Databricks applicationWhere experts can share with any use in the organization are not in the work area. This allows control panel owners to share dashboards or AI/BI applications with any identity ID ID Entra – even those that are not yet in databricks – for trouble -free and secure cooperation. New users are automatically provided only when shared content is highlighted and only inherits a grant of specific permissions, which ensures that they see and use only what they are entitled. It saves time for administrators and facilitates exsen data knowledge across their teams. For details, see our running blog.
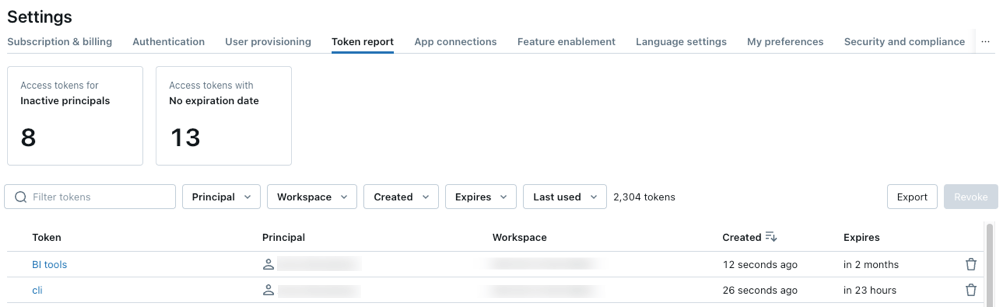
Monitor and manage personal access tokens with new administrative tools
Take control of personal access tokens (PATS) with new tokens monitoring tools now in public view across AWS,, Azureand GCP. While we recommend using OAuth Access Tokens Instatead of Pats to improve security, these monitoring tools help reduce the risk and improvise access hygiene by providing full visibility to active Pat, and enforcing time limits and allowing compromise tokens to be rapidly canceled.
Administrators now have access to this information through the new Token Tab in the console databricks admin. From there, account administrators can find active tokens concerning specific users or workspaces. You can use it to find older chips that have been set to your expiration, or those that are still active but have been actively used in a month. In particular, we recommend looking for personal approach tokens that are harassing work space administrators and appeal if they are Sunday.
Secure Program Access with Federation of OAUTH token
In order to help customers to ensure API -based access, we are excited to announce the added support for the Federation of the OAUTH token AWS,, Azureand GCP. Federation of tokens allows applications to verify databricks using tokens from your throm, eliminating the need to store the secrets of databricks, such as static tokens or passwords.
You can configure the tokens federation on two levels:
- Throughout the account: Allows a token federation for all users and a network of services on your account. For organizations knowing security they want to enforce, they consist of checks in all workloads
- Individual level of senior service (also known as the Federation of Labor Identity): To implement fine -grained checks over specific applications
The OAuth Token Federation is particularly strong for customers who drive a large number of services. For example, if you use 100+ service networks for GITHUB events, you can migrate them!
Account administrators can configure the Federation policy at a birthday level using Databricks Air Version of 0.239.0 and higher or databricks Cunt and main service Token Federation Rest API.
How do we strengthen the authentication on the databricks
In addition to the new product capabilities, we also lead an example in our business environment. In addition to the centralized single login, we assumed on the databricks:
- Hardware multi -factor verification via Fido2
- Contextual verification that involves the confidence of the device, geolocation and behavior patterns
- Automated response to detecting a broken password from our news information sources
- Crossing from quarterly to annual change of forced password to support better passwords
- Permissions at least privileges at the data level, so a user who needs access to a non -standard table could only be allowed for this table of other roles.
In summary, this provides our employees with direct access to resources while holding a strong security hold.
This is here your Way of Security Security Security on Databricks
When you have just started with MFA or are ready to accept complete automation, it has databricks tools and integration that supports you at every step.
If you want to reduce your security risk and take full advantage of these capacitives, we recommend the following proven procedures:
- Enable SSO at your account level
- Require MFA for all users
- Use OAuth Federation for Access API
- Monitor verification protocols for unusual activity
If you are ready to immerse yourself quickly, our guide to the best identity practice AWS,, Azure and GCP There are a good place to start.
Join the team and the engineering team for identity management and access to the data + AI summit, 9 – 12 June at the Moscon Center in San Francisco! Get a first view of late innovations in data and management AI and see our identity and access management sessions:
Sign up now and secure your place!